Securing the Future of Industry: How ICS Security Is Evolving with IT/OT Convergence
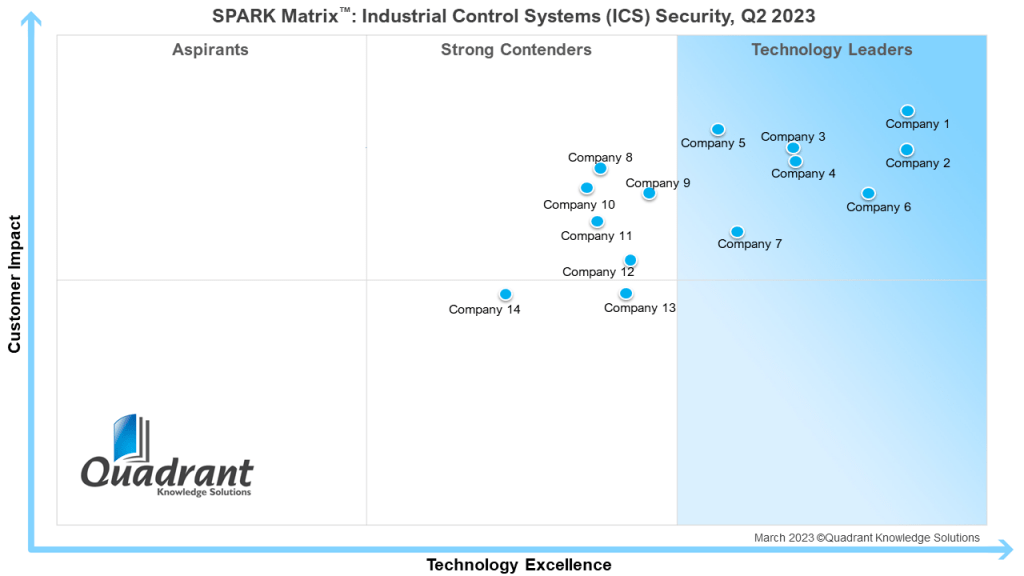
Industrial control systems (ICS) sit at the heart of modern manufacturing, energy, transportation, and utilities. As operational technology (OT) environments become increasingly connected—to corporate IT networks, cloud platforms, and a growing array of Industrial Internet of Things (IIoT) devices—the attack surface expands dramatically.
Today’s ICS security market is responding to that reality: vendors are blending deep OT domain knowledge with advanced intelligent tools, research-driven threat intelligence, and strategic partnerships to deliver customer-centric solutions that emphasize cyber resilience and, critically, total asset visibility.
Why IT/OT convergence changes the game
Historically, OT environments were isolated and designed for reliability and determinism, not cybersecurity. That model is changing fast. Driven by efficiency goals, predictive maintenance, and digital transformation initiatives, organizations are connecting legacy PLCs, SCADA systems, HMIs, sensors, and actuators to enterprise networks and cloud services.
While this connectivity unlocks powerful operational benefits—real-time analytics, remote monitoring, and automated optimization—it also introduces new vulnerabilities. An attacker who gains a foothold in IT can — through poorly segmented links or vulnerable gateways — reach mission-critical OT assets that control physical processes.
This convergence demands a fundamentally different security posture: one that understands industrial protocols, process safety constraints, and the life-cycle of OT assets, while also leveraging modern IT security capabilities.
The evolving threat landscape
Threat actors targeting ICS aren’t just opportunistic ransomware gangs anymore; the ecosystem now attracts sophisticated nation-state actors, advanced persistent threats (APTs), hacktivists, and supply-chain adversaries. Attack vectors include:
- Exploited legacy systems and default credentials on OT devices
- Compromised remote access tools used for maintenance
- Malicious firmware updates and tampered supply-chain components
- Lateral movement from IT to OT due to weak segmentation
- IIoT devices with minimal security hardening acting as beachheads
Consequences are not limited to data loss—disruption can cause downtime, material loss, safety incidents, environmental damage, and regulatory exposure. That’s why the market emphasis has shifted from simple perimeter defenses to resilience, detection, and rapid recovery.
Intelligent tools and visibility: the foundation of resilience
A recurring theme among modern ICS security offerings is total asset visibility. You can’t protect what you can’t see. Vendors combine passive network monitoring, active discovery, and agentized telemetry to create a single inventory of PLCs, RTUs, HMIs, embedded controllers, and IIoT endpoints.
When paired with contextualized asset risk scoring—taking into account firmware versions, known vulnerabilities, communication patterns, and process criticality—teams gain the situational awareness needed to prioritize remediation.
On top of visibility, AI and machine-learning-driven anomaly detection play a growing role. Behavioral baselining models learn normal process and network behavior, surfacing deviations that static rules would miss.
This reduces detection time for subtle attacks like command injection or stealthy lateral movement and helps distinguish true threats from benign operational anomalies—crucial in environments where false positives can be costly.
Strategic partnerships and industry research accelerate capability
No single vendor can cover every OT niche. As a result, the market is marked by partnerships between cybersecurity firms, OT specialists, system integrators, and cloud providers. Collaborative research—often industry-sponsored—helps uncover attack patterns specific to sectors such as energy, pharmaceuticals, or manufacturing.
These partnerships yield tailored threat intelligence feeds, hardened reference architectures, and tested incident playbooks, enabling providers to offer customer-centric services that respect process safety and regulatory needs.
From products to services: MDR, IR, and managed OT security
Many organizations lack in-house OT security expertise, and building it is expensive and time-consuming. Managed Detection and Response (MDR) for OT, incident response (IR) retainers, and security operations center (SOC) services specialized in ICS are growing rapidly.
These services combine remote monitoring, threat hunting, forensic analysis, and on-call OT responders who understand both cyber and control-system implications—delivering practical, operationally safe actions during an incident.
Practical controls that make a difference
Successful ICS security programs blend technology with process and governance:
- Network segmentation & micro-segmentation: Limit lateral movement between IT and OT zones and within OT tiers.
- Secure remote access & credential management: Enforce multi-factor authentication (MFA), just-in-time access, and vaulting for privileged credentials.
- Patch and firmware management: Where possible, maintain a rigorous, risk-aware update cadence that respects process availability.
- Network-based detection: Use passive monitoring to avoid disrupting critical systems while collecting rich telemetry.
- Incident playbooks & tabletop exercises: Prepare teams with OT-aware response plans that prioritize safety and continuity.
- Supply-chain risk assessments: Vet vendors for secure development practices and firmware integrity measures.
- Continuous training: Upskill both IT and OT personnel so they can collaborate during detection and response.
Regulatory and compliance pressures
Regulators and industry standards are tightening expectations for critical infrastructure. Compliance frameworks, whether sector-specific or national, increasingly require demonstrable asset visibility, logging, access controls, and incident reporting. Providers that bake compliance into solutions—offering auditable controls and automated evidence collection—gain a competitive advantage.
The road ahead: predictive security and cyber-digital twins
Looking forward, two trends stand out. First, predictive security—leveraging digital twins and advanced analytics to forecast failure modes and likely attack paths—will move from labs to operations. Digital twins that simulate both the physical process and its cyber footprint allow safe testing of patches, configuration changes, and attack scenarios.
Second, continued fusion of AI with domain expertise will improve threat detection precision and automate routine containment tasks, freeing human experts for strategic work.
Conclusion
The Industrial Control Systems (ICS) security market is maturing into an ecosystem that balances deep industrial domain knowledge with cutting-edge cybersecurity practices. As IT/OT convergence and IIoT adoption accelerate, organizations must prioritize total asset visibility, intelligent detection, and resilient operational practices.
Vendors succeeding in this space are those who combine research-driven tools, strategic partnerships, and operationally aware services to deliver not just protection, but the ability to keep critical infrastructure safe and running—under attack or in peace.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Games
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



